Featured Post
Mobile Device Threats
- Dapatkan link
- X
- Aplikasi Lainnya
Mobile Device Threats. Without mobile device security measures, organizations can be vulnerable to malicious software, data leakage and other mobile threats. 5 ways your mobile device can get malware.
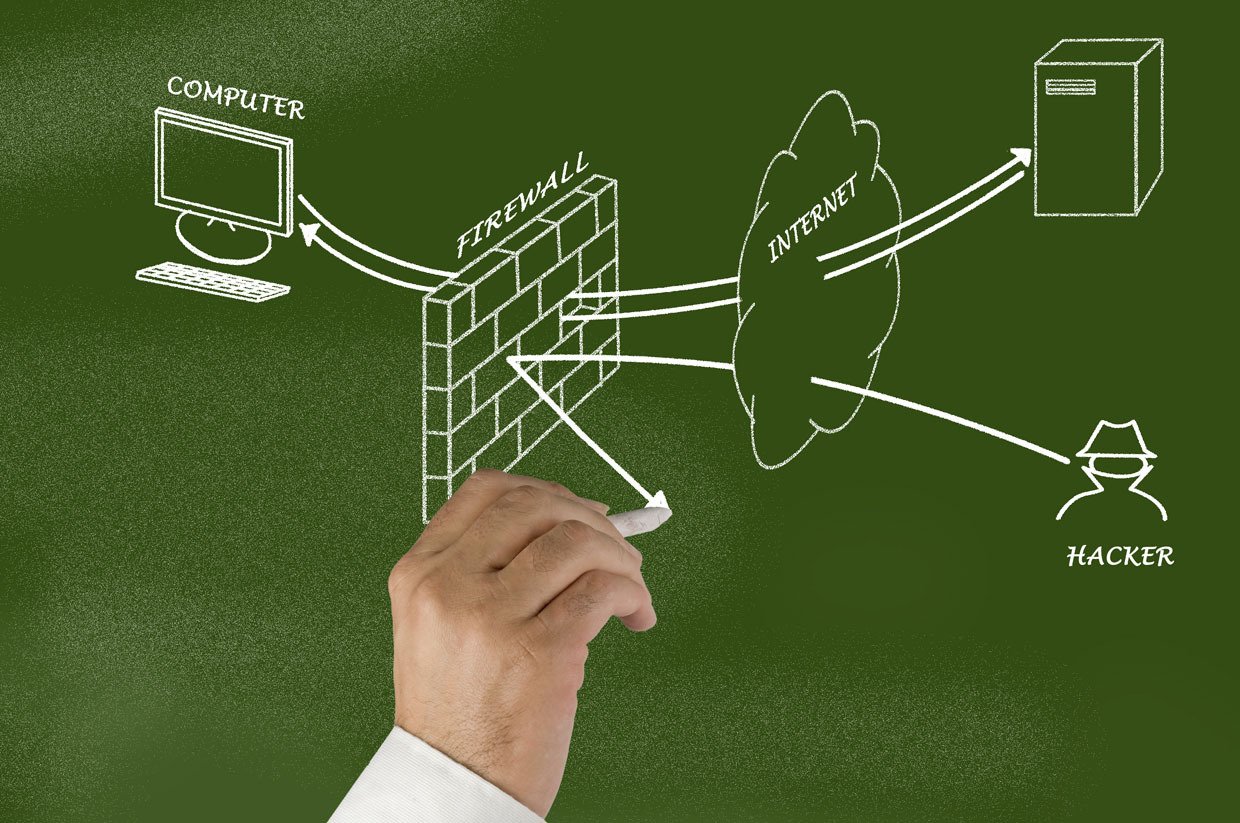
Email phishing is a common attack on. As mobile devices become increasingly important, they have received additional attention from cybercriminals. Physical threats to mobile devices most commonly refer to the loss or theft of a device.
Once a mobile device is infected with madware from a malicious app, ads can infiltrate almost every aspect on a user’s phone.
And 78% of those files were malware programs, meaning that over 280,000 malware files per. 5 ways your mobile device can get malware. Assessing threats to mobile devices & infrastructure:
Phones in the office are threatening your business and you may not even realize it.
As one type of sms attack, these and other threats in the category pose a significant threat to all mobile users. As mobile devices become increasingly important, they have received additional attention from cybercriminals. Criminal syndicates are strategically adapting to the changing times.
The report has found that mobile device security is improving, and advances have been made by mobile operating systems providers.
This research summarizes the findings of their work performing cyber security assessment of mobile apps for ios and android in 2018, most common vulnerabilities to mobile devices and prevention recommendations to users and developers Mobile device security threats are on the rise. Mobile device management and enterprise mobility
Positive technologies experts regularly perform security threats analysis of mobile applications.
Cloud mdm services that leverage the federal risk and authorization management program (fedramp), for example, can increase confidence in the security of these solutions with consistent security authorizations using a. Using our phones for sensitive business. Only 20 percent of android devices are running the newest version and only 2.3 percent are on the latest release.
8 • phishing attacks use electronic communications to trick users into installing malicious software or giving away sensitive information.
Also learn about android security threats and specific vulnerabilities. Device that has a vulnerable application or network service running in the background. Mobile device deployments introduce new threats to organizations, including advanced malware, data leakage, and the disclosure to attackers of enterprise secrets, intellectual property, and personally identifiable information assets.
- Dapatkan link
- X
- Aplikasi Lainnya
Komentar
Posting Komentar